
Home Security Products
Mobile & Home Products:
Technical Support Services:
Who are The Usual Suspects and what can you do to keep yourself safe from them?
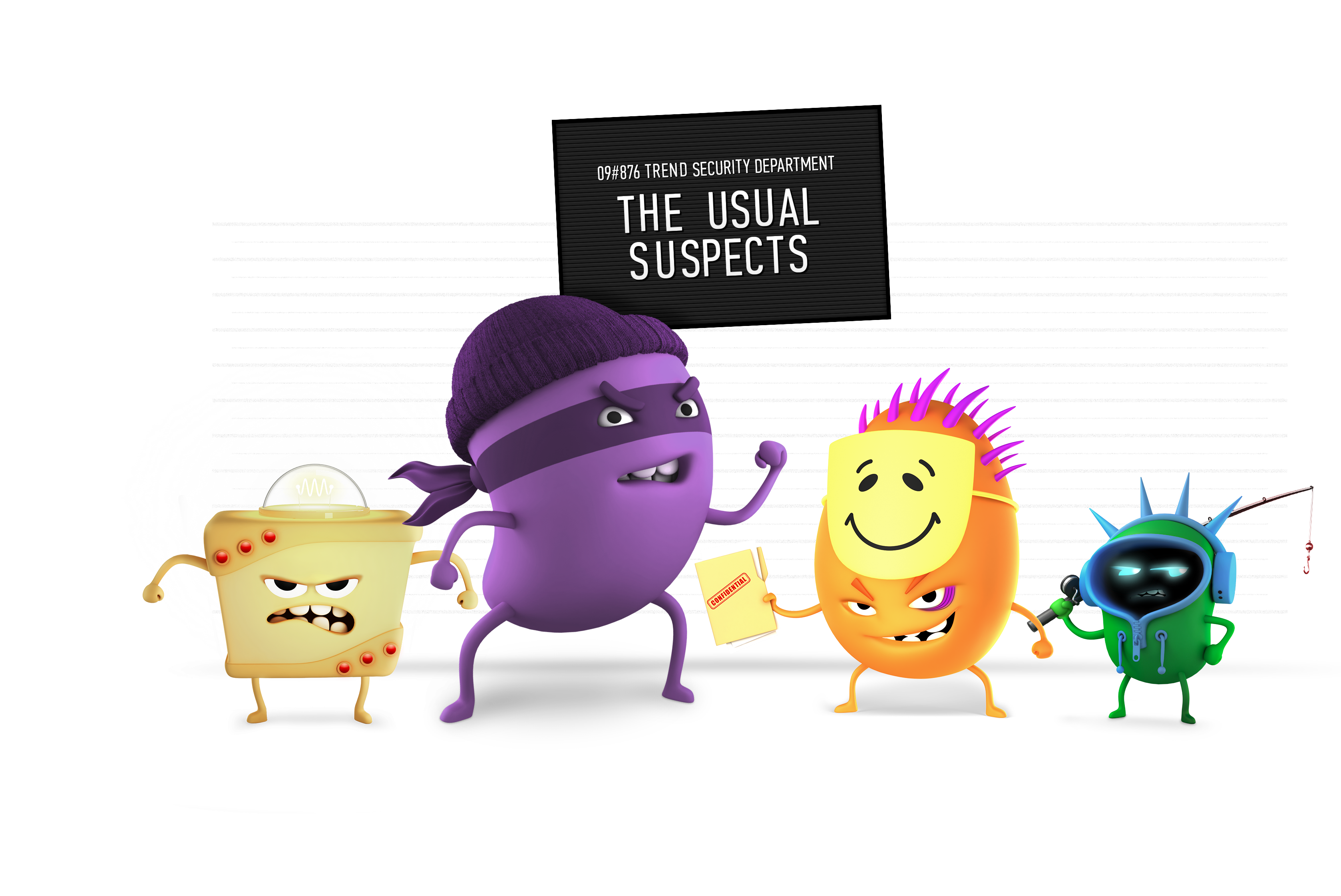

Wanted for: Slipping malware into emails and downloadable content
Specialty: Computers and laptops, mobiles
A born trickster, The Malware is an expert at hiding malicious links in emails and attachments. Never one to shy away from a challenge, he creates urgency and panic in his victims to ensure they believe his malicious intent.
After building a vast database of legitimate organisations to impersonate, he spreads his malware far and wide to ensure any person; young or old, tech savvy or not, will be conned into clicking a link and giving immediate access to their computer or laptop.
Beginning a life of crime early, his lack of compassion is only matched by an equally horrendous spelling and grammatical aptitude.
Wanted for: Breaking and entering to steal personal information
Specialty: Smart home devices
Beginning his career breaking into PCs and mobile devices, The Network Intruder has moved on to smart home devices as devious way to steal personal information.
These include a worrying new speciality of suburban street prowling, looking for unprotected smart home devices like smart TVs, gaming consoles and security cameras in order to invade the home network.
The Network Intruder moves through all the smart devices on the network to look for weaknesses to exploit. This can include using cameras to see inside the home, collecting personal information, images and videos from devices, and even using the home network as their base to conduct malicious attacks back onto the internet, all unbeknownst to the unsuspecting household.


Wanted for: Maliciously attacking and spoofing text messages
Specialty: Mobile phones, PC, Notebooks
A shadowy underground figure, The Phisher is known for carefully crafting text messages to masquerade as legitimate businesses in order to ‘fish’ for credit card details, passwords and banking logins. He achieves all this while pumping his obscure Norwegian death metal.
Currently on the run from several world governments due to his phishing scam ring being compromised, The Phisher is laying low by targeting his attacks to specific mobile phone users.
In addition to his text message phishing scams, he employs; spoofing on public WiFi networks, attacks poorly secured mobile apps and gains access to mobile phones to engage in identity theft. This all lays the groundwork for more elaborate, widespread phishing scams.
Wanted for: Identity theft
Specialty: Stealing personal information for financial gain
The Identity Thief has been around for years, stealing personal information via malware, scams, hacks and data breaches.
The information he steals can range from credit card information to driver’s license numbers, tax file numbers and even passport numbers.
With every piece of information stolen, The Identity Thief looks to impersonate you to access as much money as he can; whether it be via opening credit cards, accessing bank funds or by selling the information on the Dark Web, all before discarding the identity and assuming a new one.
He leaves a destruction in his wake with victims left to pick up the pieces of their stolen identity, with many even unaware of this invasion of privacy.

Trend Micro Device Security Ultimate provides complete device and identity protection for you and your family. Protect your PC, Mac, mobile phones, tablets and smart devices from all these threats and more.
- Antivirus, malware and spyware protection
- Guards against identity theft with Dark Web monitoring
- Secure VPN to protect your privacy
- Keep your children safe online
- Protect and manage passwords
- Protect and manage smart devices such as smart TVs and gaming consoles

Who are The Usual Suspects and what can you do to keep yourself safe from them?

 THE MALWARE
THE MALWARE
Wanted for: Slipping malware into emails and downloadable content
Specialty: Computers and laptops, mobiles
A born trickster, The Malware is an expert at hiding malicious links in emails and attachments. Never one to shy away from a challenge, he creates urgency and panic in his victims to ensure they believe his malicious intent.
After building a vast database of legitimate organisations to impersonate, he spreads his malware far and wide to ensure any person; young or old, tech savvy or not, will be conned into clicking a link and giving immediate access to their computer or laptop.
Beginning a life of crime early, his lack of compassion is only matched by an equally horrendous spelling and grammatical aptitude.
 THE NETWORK INTRUDER
THE NETWORK INTRUDER
Wanted for: Breaking and entering to steal personal information
Specialty: Smart home devices
Beginning his career breaking into PCs and mobile devices, The Network Intruder has moved on to smart home devices as devious way to steal personal information.
These include a worrying new speciality of suburban street prowling, looking for unprotected smart home devices like smart TVs, gaming consoles and security cameras in order to invade the home network.
The Network Intruder moves through all the smart devices on the network to look for weaknesses to exploit. This can include using cameras to see inside the home, collecting personal information, images and videos from devices, and even using the home network as their base to conduct malicious attacks back onto the internet, all unbeknownst to the unsuspecting household.
 THE PHISHER
THE PHISHER
Wanted for: Maliciously attacking and spoofing text messages
Specialty: Mobile phones, PC, Notebooks
A shadowy underground figure, The Phisher is known for carefully crafting text messages to masquerade as legitimate businesses in order to ‘fish’ for credit card details, passwords and banking logins. He achieves all this while pumping his obscure Norwegian death metal.
Currently on the run from several world governments due to his phishing scam ring being compromised, The Phisher is laying low by targeting his attacks to specific mobile phone users.
In addition to his text message phishing scams, he employs; spoofing on public WiFi networks, attacks poorly secured mobile apps and gains access to mobile phones to engage in identity theft. This all lays the groundwork for more elaborate, widespread phishing scams.
 THE IDENTITY THIEF
THE IDENTITY THIEF
Wanted for: Identity theft
Specialty: Stealing personal information for financial gain
The Identity Thief has been around for years, stealing personal information via malware, scams, hacks and data breaches.
The information he steals can range from credit card information to driver’s license numbers, tax file numbers and even passport numbers.
With every piece of information stolen, The Identity Thief looks to impersonate you to access as much money as he can; whether it be via opening credit cards, accessing bank funds or by selling the information on the Dark Web, all before discarding the identity and assuming a new one.
He leaves a destruction in his wake with victims left to pick up the pieces of their stolen identity, with many even unaware of this invasion of privacy.
 Trend Micro Device Security Ultimate provides complete device and identity protection for you and your family. Protect your PC, Mac, mobile phones, tablets and smart devices from all these threats and more.
Trend Micro Device Security Ultimate provides complete device and identity protection for you and your family. Protect your PC, Mac, mobile phones, tablets and smart devices from all these threats and more.
- Antivirus, malware and spyware protection
- Guards against identity theft with Dark Web monitoring
- Secure VPN to protect your privacy
- Keep your children safe online
- Protect and manage passwords
- Protect and manage smart devices such as smart TVs and gaming consoles